Malicious VS Code Mimic As Zoom App Steals Cookies From Chrome
Cybersecurity researchers have uncovered a new threat targeting developers using Visual Studio Code (VS Code). A malicious extension masquerading as a Zoom app has been discovered stealing cookies from Google Chrome, raising concerns about the security of the VS Code extension ecosystem. The deceptive extension, uploaded to the VS Code Marketplace on November 30, 2024, […] The post Malicious VS Code Mimic As Zoom App Steals Cookies From Chrome appeared first on Cyber Security News.

Cybersecurity researchers have uncovered a new threat targeting developers using Visual Studio Code (VS Code).
A malicious extension masquerading as a Zoom app has been discovered stealing cookies from Google Chrome, raising concerns about the security of the VS Code extension ecosystem.
The deceptive extension, uploaded to the VS Code Marketplace on November 30, 2024, and last updated on December 8, impersonates the Zoom Workspace tool.
To enhance its credibility, the uploader included a link to the legitimate GitHub repository for the Zoom Meeting SDK.
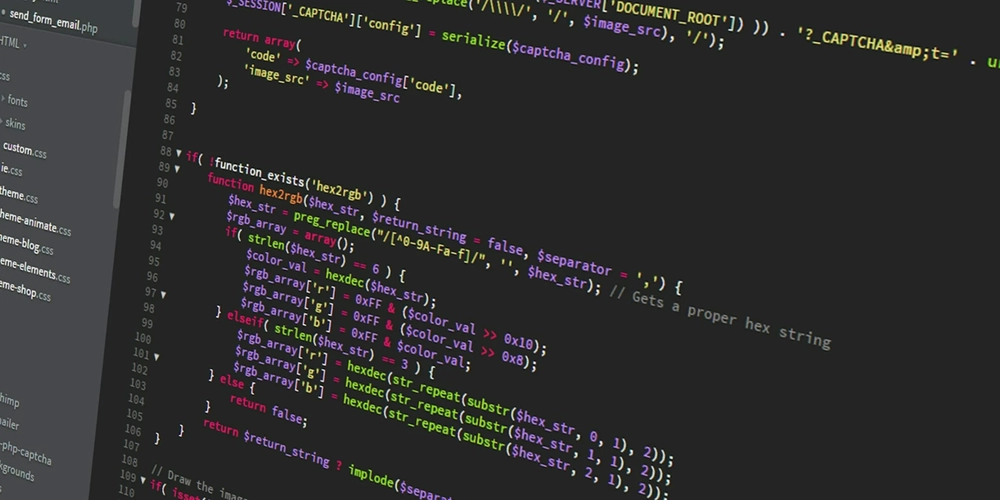
The malicious extension’s core functionality is contained in two main files:-
- ./dist/extension.js: Responsible for activating and deactivating the extension.
- ./src/extension-web.js: Contains the extension’s primary logic.
Researchers at Hunt.io identified that the extension is activated using the “onStartupFinished” event in the package.json file, ensuring that any malicious code runs once VS Code has fully loaded.
.webp)
Key Components:-
- The extension uses various Node.js modules, including sqlite3 for database interactions and path and os for system-specific operations.
- A suspicious endpoint is declared: ‘https://api.storagehb.cn/d?v=1.3’, pointing to a server hosted in China.
- The code attempts to access Chrome’s cookie storage and Windows registry data related to security accounts.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
A Fraudulent VS Code Extension
An SQL query is used to extract sensitive information from the Chrome cookies database:-
SELECT host_key, name, encrypted_value, path, expires_utc, is_secure, is_httponly, creation_utc, has_expires, is_persistent FROM cookies.webp)
This query retrieves various cookie attributes, including encrypted values, expiration dates, and security flags.
The extension was initially released as versions 0.2.0 and 0.2.1 on November 30, with the code targeting Google Chrome cookies introduced in version 0.2.2 on December 8. This suggests a deliberate strategy to bypass early detection mechanisms.
This discovery highlights the potential security risks associated with VS Code extensions. Developers are advised to:
- Thoroughly vet extensions before installation, including code audits and reputation checks.
- Implement strict access controls, limiting extension permissions to only what’s necessary.
- Stay informed about potential security threats in development environments.
Cybersecurity experts have reported the malicious extension to the Microsoft VS Code Marketplace to protect users.
As IDEs like VS Code continue to be essential tools for developers, maintaining vigilance and implementing robust security practices becomes increasingly crucial to safeguard sensitive data and maintain the integrity of software development processes.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
The post Malicious VS Code Mimic As Zoom App Steals Cookies From Chrome appeared first on Cyber Security News.
What's Your Reaction?