The great Google Ads heist: criminals ransack advertiser accounts via fake Google ads
An ongoing malvertising campaign steals Google advertiser accounts via fraudulent ads for Google Ads itself.

Table of contents
- Overview
- Criminals impersonate Google Ads
- Lures hosted on Google Sites
- Phishing for Google account credentials
- Victimology
- Who is behind these campaigns?
- Fuel for other malware and scam campaigns
- Indicators of Compromise
Overview
Online criminals are targeting individuals and businesses that advertise via Google Ads by phishing them for their credentials — ironically — via fraudulent Google ads.
The scheme consists of stealing as many advertiser accounts as possible by impersonating Google Ads and redirecting victims to fake login pages. We believe their goal is to resell those accounts on blackhat forums, while also keeping some to themselves to perpetuate these campaigns.
This is the most egregious malvertising operation we have ever tracked, getting to the core of Google’s business and likely affecting thousands of their customers worldwide. We have been reporting new incidents around the clock and yet keep identifying new ones, even at the time of publication.
The following diagram illustrates at a high level the mechanism by which advertisers are getting fleeced:

Criminals impersonate Google Ads
Advertisers are constantly trying to outbid each other to reach potential customers by buying ad space on the world’s number one search engine. This earned Google a whopping $175 billion in search-based ad revenues in 2023. Suffice to say, the budgets spent in advertising can be considerable and of interest to crooks for a number of reasons.
We first started noticing suspicious activity related to Google accounts somewhat accidentally, and after a deeper look we were able to trace it back to malicious ads for… Google Ads itself! Very quickly we were overwhelmed by the onslaught of fraudulent “Sponsored” results, specifically designed to impersonate Google Ads, as can be seen in Figure 2:
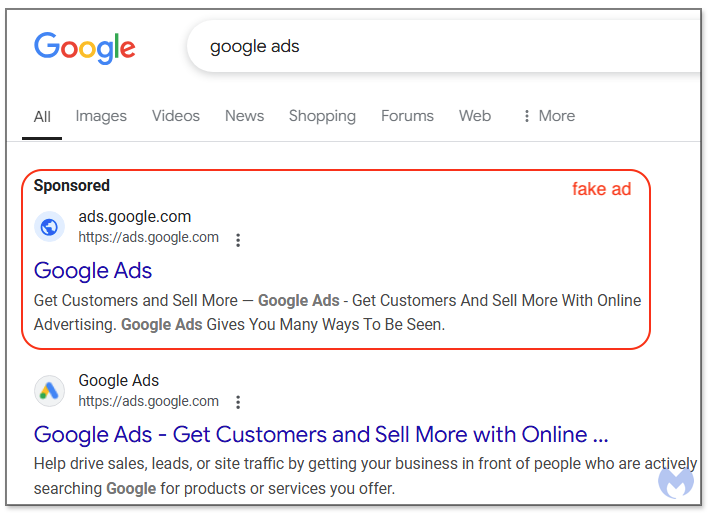
While it is hard to believe such a thing could actually happen, the proof is there when you click on the 3-dot menu that shows more information about the advertiser. We have partially masked the victim’s name, but clearly it is not Google; they are just one of the many accounts that have already been compromised and abused to trick more users:

People who will see those ads are individuals or businesses that want to advertise on Google Search or already do. Indeed, we saw numerous ads specifically for each scenario, sign up or sign in, as seen in Figure 4:

The fake ads for Google Ads come from a variety of individuals and businesses, in various locations. Some of those hacked accounts already had hundreds of other legitimate ads running, and one of them was for a popular Taiwanese electronics company.

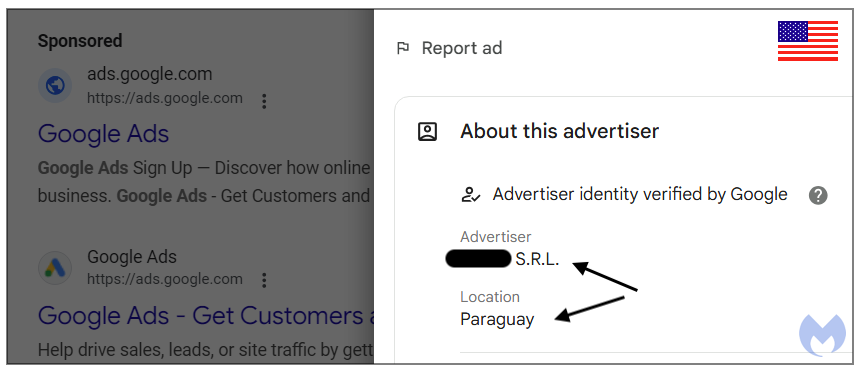
To get an idea of the geographic scope of these campaigns, we performed the same Google search simultaneously from several different geolocations (using proxies). First, here’s the malicious ad from a U.S. IP address belonging to a business registered in Paraguay:
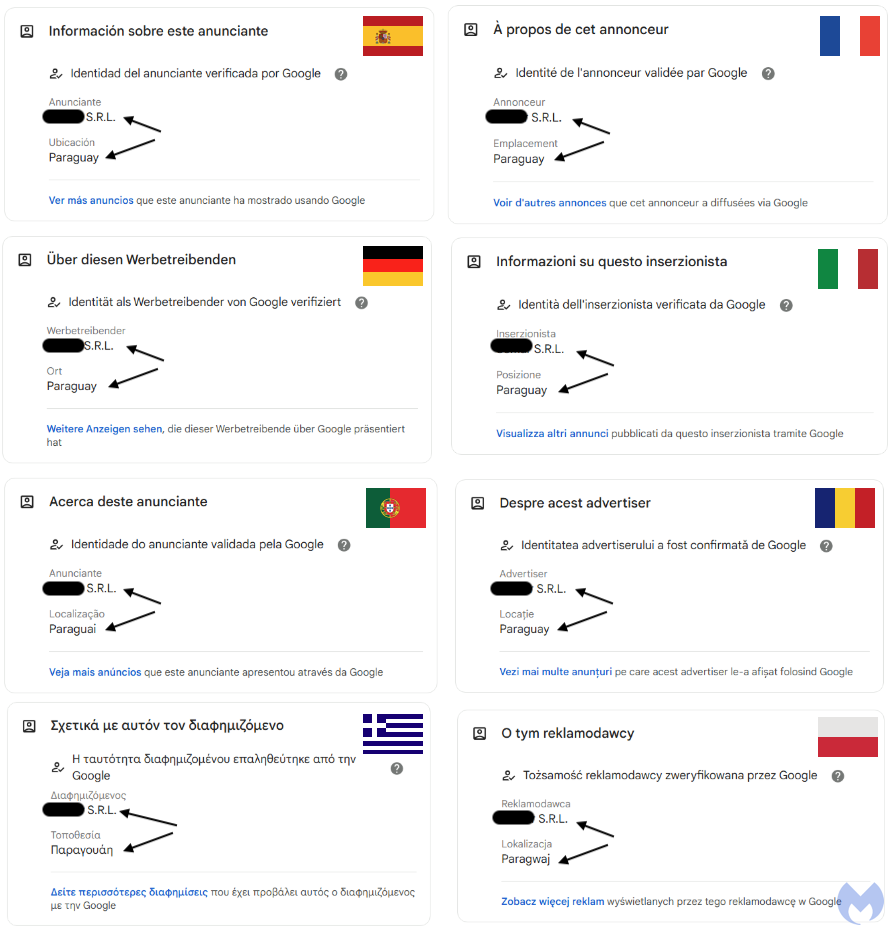
Now, here’s that same ad that appears on Google Search in several other countries:
Lures hosted on Google Sites
Once victims click on those fraudulent ads, they are redirected to a page that looks like Google Ads’ home page, but oddly enough, it us hosted on Google Sites. These pages act as a sort of gateway to external websites specifically designed to steal the usernames and passwords from the coveted advertisers’ Google accounts.

There’s a good reason to use Google Sites, not only because it’s a free and a disposable commodity but also because it allows for complete impersonation. Indeed, you cannot show a URL in an ad unless your landing page (final URL) matches the same domain name. While that is a rule meant to protect abuse and impersonation, it is one that is very easy to get around.

Looking back at the ad and the Google Sites page, we see that this malicious ad does not strictly violate the rule since sites.google.com uses the same root domains ads ads.google.com. In other words, it is allowed to show this URL in the ad, therefore making it indistinguishable from the same ad put out by Google LLC..
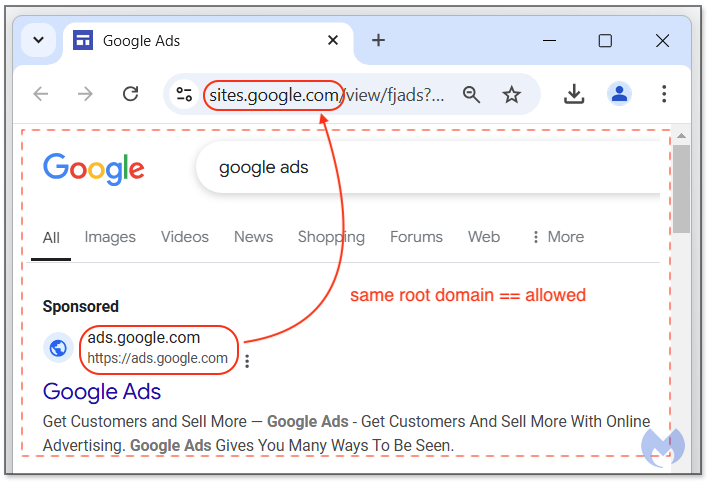
Phishing for Google account credentials
After the victims click on the “Start now” button found on the Google Sites page, they are redirected to a different site which contains a phishing kit. JavaScript code fingerprints users while they go through each step to ensure all important data is being surreptitiously collected.
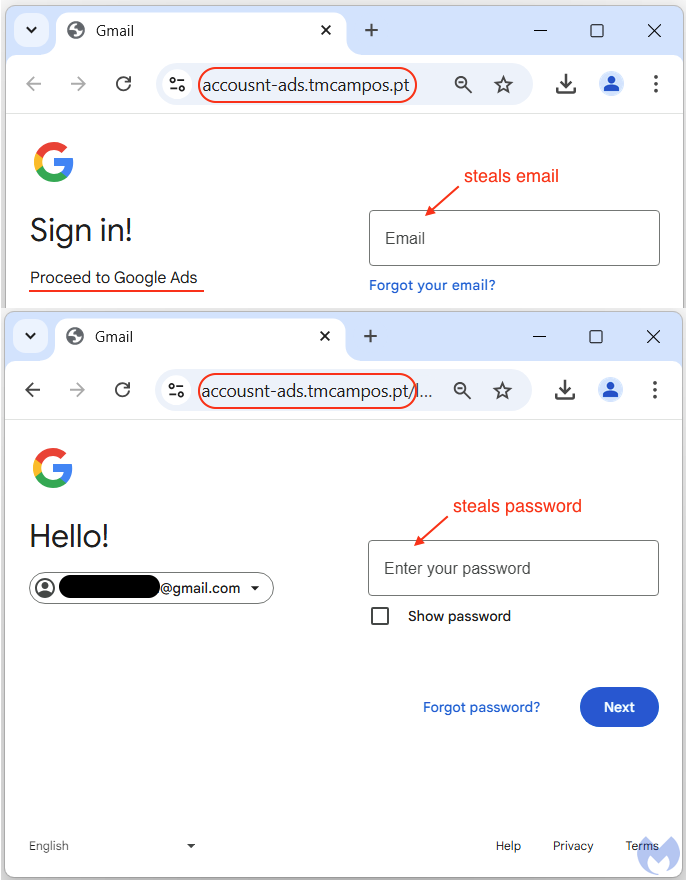
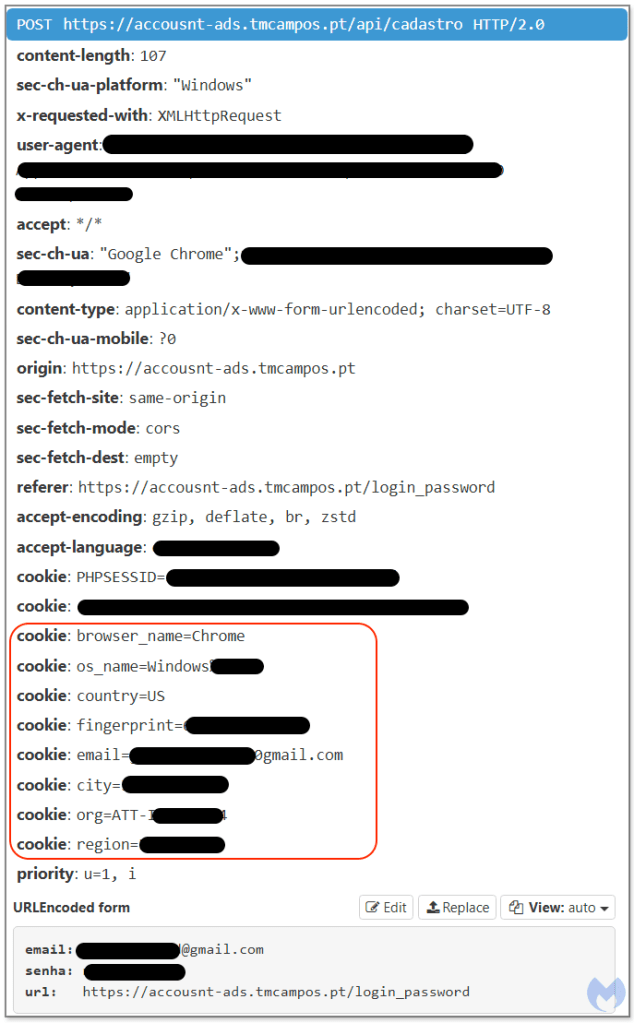
Finally, all the data is combined with the username and password and sent to the remote server via a POST request. We see that criminals even receive the victim’s geolocation, down to the city and internet service provider.
Victimology
There are multiple online reports of people who saw the fake Google Ads and shared their experiences:
- Help with removing a dangerous scam in Google Ads (Google Ads Help forum)
- Google Ads Phishing Scam (Reddit)
- It’s just me or Google just sponsored a link to a phising site for Google ads? (Reddit)
- Be aware of fake google page, clicked by accident (Reddit)
- Warning! First sponsorized google answer for “Google ads” is a phishing attempt ! (BlueSky)
We were able to get in touch with a couple of victims who not only saw the ads but were actually scammed and lost money. Thanks to their testimony and our own research, we have a better idea of the criminals’ modus operandi:
- Victim enters their Google account information into phishing page
- Phishing kit collects unique identifier, cookies, credentials
- Victim may receive an email indicating a login from an unusual location (Brazil)
- If the victim fails to stop this attempt, a new administrator is added to the Google Ads account via a different Gmail address
- Threat actor goes on a spending spree, locks out victim if they can
Who is behind these campaigns?
We identified two main groups of criminals running this scheme but the more prolific by far is one made of Portuguese speakers likely operating out of Brazil. Victims have also shared that they had received a notification from Google indicating suspicious logins from Brazil. Unfortunately, those notifications often came too late or where dismissed as legitimate, and the criminals already had time to do some damage.
We should also note a third campaign that is very different from the other two, and where the threat actors’ main goal is to distribute malware. The Google Ads phishing scheme may have been a temporary run which was not their main focus.
Brazilian team
In the span of a few days, we reported over 50 fraudulent ads to the Google Ad team all coming from this Brazilian group. We quickly realized that no matter how many reported incidents and takedowns, the threat actors managed to keep at least one malicious ad 24/7.
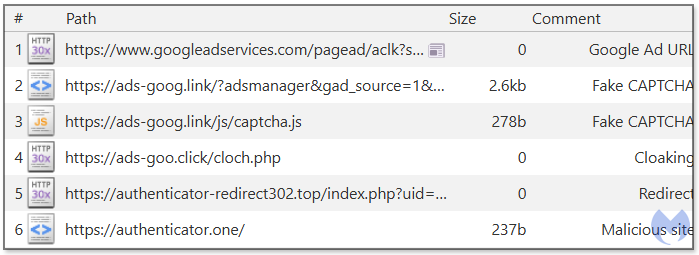
Figure 13 shows the network traffic resulting from a click on the ad. You will see multiple hops before finally arriving to the phishing portal. The second URL shows the crooks are using a paid service to detect fake traffic.

Within the JavaScript code part of the phishing kit, there are comments in Portuguese. Figure 14 shows a portion of the code that does browser fingerprinting, which is a way of identifying users. Browser language, system CPU, memory, screen-width, and time zone are some of the data points collected and then hashed.

Asian team
The second group is using advertiser accounts from Hong Kong and appears to be Asia-based, perhaps from China. Interestingly, they also use the same kind of delivery chain by leveraging Google sites. However, their phishing kit is entirely different from their Brazilian counterparts.
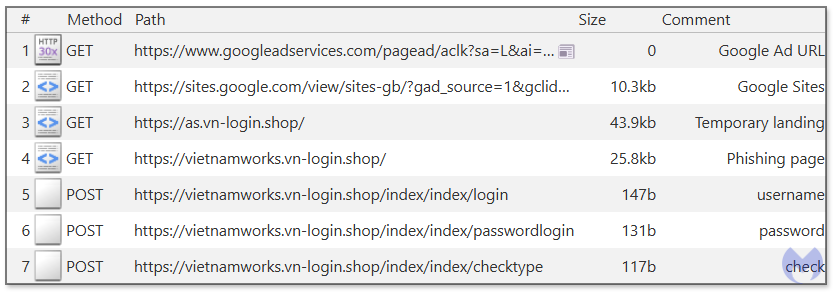
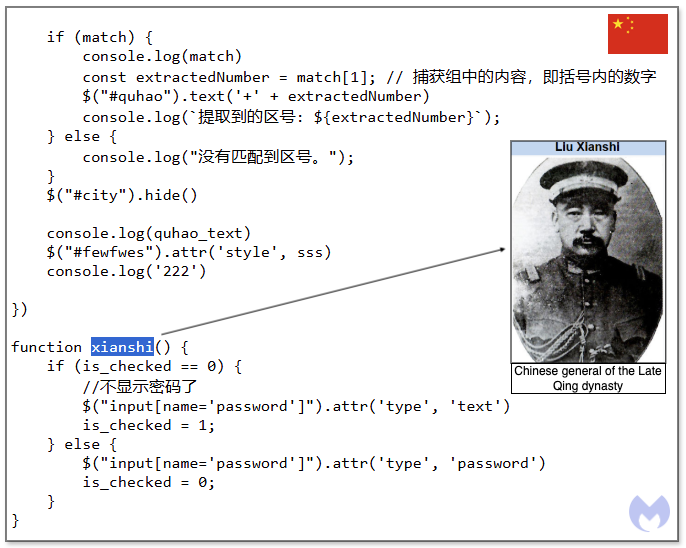
Figure 16 below shows a code extract with comments in Chinese, as well as a function called xianshi, which could be in reference to a Chinese general of the late Qing dynasty or even a superhero from more modern gaming and literature.
Third campaign (possibly Eastern European)
We observed another campaign which has a very different modus operandi. Google Sites is not involved at all, and instead they rely on a fake CAPTCHA lure and heavy obfuscation of the phishing page.
Interestingly, the malicious ad we found was for Google Authenticator, despite the obvious ads-goo[.]click domain name. However, for about day or so, the redirect from that domain lead directly to a phishing portal hosted at ads-overview[.]com.
The reason why we suggest the threat actors may be Eastern Europeans here is because of the type of redirects and obfuscation. There is also a distant feel of ‘software download via Google ads’ we have reported on previously (see Threat actor impersonates Google via fake ad for Authenticator).
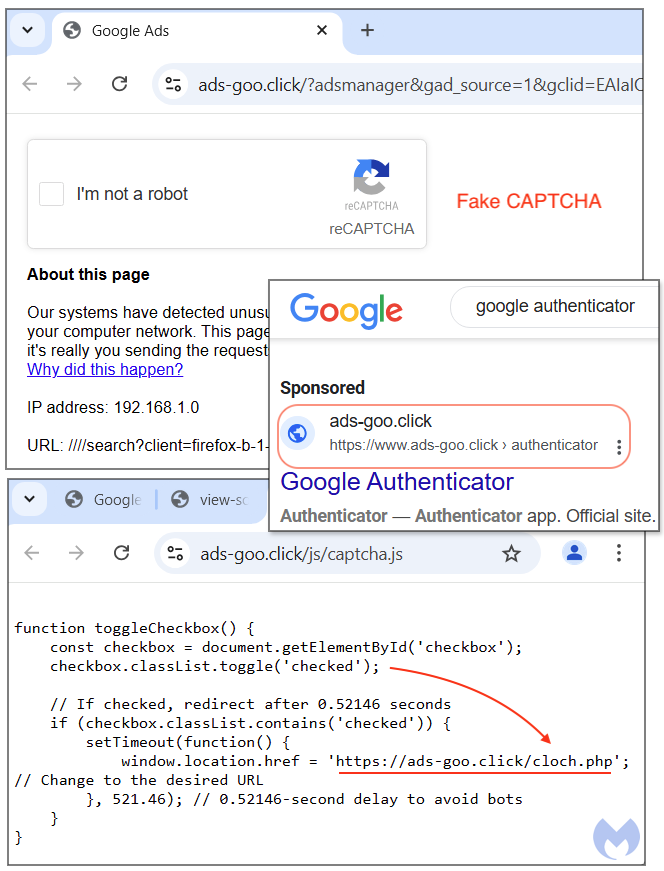
A PHP script (cloch.php) then determines if the visitor is genuine or not (likely doing a server-side IP check). VPNs, bot and detection tools will get a “white” page showing some bogus instructions on how to run a Google Ads campaign. Victims are instead redirected to ads-overview[.]com which is a phishing portal for Google accounts.
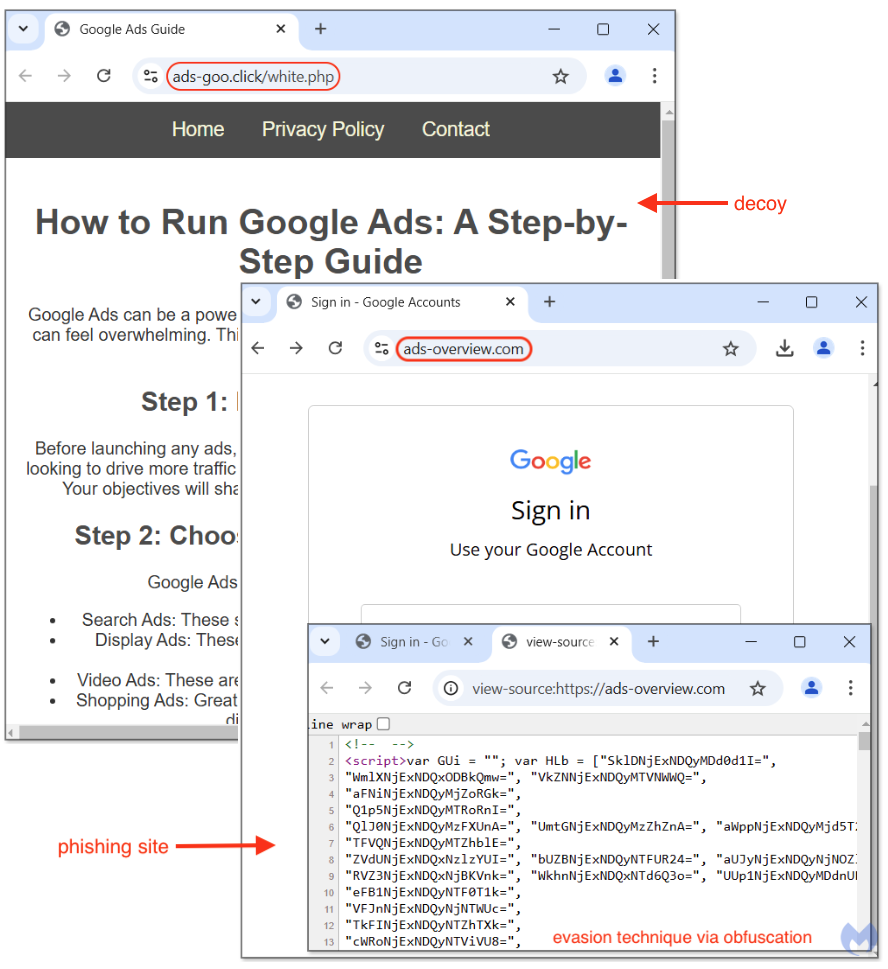
When we checked back on this campaign a few days later, we saw that the ad URL now redirected to a fake Google Authenticator site, likely to download malware. The redirection mechanism is shown in Figure 20:
Fuel for other malware and scam campaigns
Stolen Google Ads accounts are a valuable commodity among thieves. As we have detailed it many times on this blog, there are constant malvertising campaigns leveraging compromised advertiser accounts to buy ads that push scams or deliver malware.
- Printer problems? Beware the bogus help
- Malicious ad distributes SocGholish malware to Kaiser Permanente employees
- Hello again, FakeBat: popular loader returns after months-long hiatus
- Large scale Google Ads campaign targets utility software
If you think about it for a second, crooks are using someone else’s budget to further continue spreading malfeasance. Whether those dollars are spent towards legitimate ads or malicious ones, Google still earns revenues from those ad campaigns. The losers are the hacked advertisers and innocent victims that are getting phished.
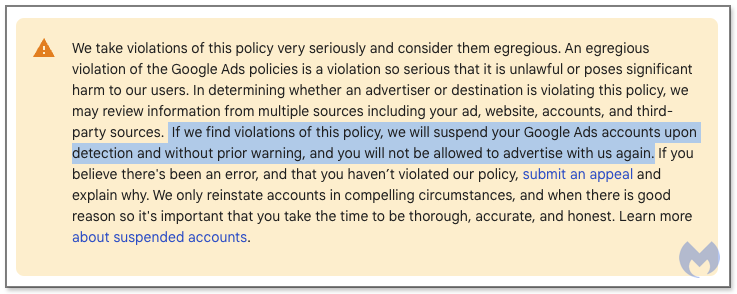
As result, taking action on compromised ad accounts plays a key part in driving down malvertising attacks. Google has yet to show that it takes definitive steps to freeze such accounts until their security is restored, despite their own policy on the subject (Figure 20). For example, we recently saw a case where the same advertiser that had already been reported 30 times, was still active.
As the scourge of fraudulent ads continues, we urge users to pay particular attention to sponsored results. Ironically, it’s quite possible that individuals and businesses that run ad campaigns are not using an ad-blocker (to see their ads and those from their competitors), making them even more susceptible to fall for these phishing schemes.
We don’t just report on threats—we block them
Cybersecurity risks should never spread beyond a headline. Keep threats off by downloading Malwarebytes Browser Guard today.
Indicators of Compromise
Fake Google Sites pages
sites[.]google[.]com/view/ads-goo-vgsgoldx
sites[.]google[.]com/view/ads-word-cmdw
sites[.]google[.]com/view/ads-word-makt
sites[.]google[.]com/view/ads-word-whishw
sites[.]google[.]com/view/ads-word-wwesw
sites[.]google[.]com/view/ads-word-xvgt
sites[.]google[.]com/view/ads3dfod6hbadvhj678
sites[.]google[.]com/view/aluado01
sites[.]google[.]com/view/ap-rei-pandas
sites[.]google[.]com/view/appsd-adsd
sites[.]google[.]com/view/asd-app-goo
sites[.]google[.]com/view/connectsing/addss
sites[.]google[.]com/view/connectsingyn/ads
sites[.]google[.]com/view/entteraccess
sites[.]google[.]com/view/exercitododeusvivo
sites[.]google[.]com/view/fjads
sites[.]google[.]com/view/goitkm/google-ads
sites[.]google[.]com/view/hdgstt
sites[.]google[.]com/view/helpp2k
sites[.]google[.]com/view/hereon/1sku4yf
sites[.]google[.]com/view/hgvfvd
sites[.]google[.]com/view/joaope-defeijao
sites[.]google[.]com/view/jthsjd
sites[.]google[.]com/view/logincosturms/ads
sites[.]google[.]com/view/logins-words-officails
sites[.]google[.]com/view/logins-words-officsdp
sites[.]google[.]com/view/marchatrasdemarcha
sites[.]google[.]com/view/newmanage/page
sites[.]google[.]com/view/one-vegas
sites[.]google[.]com/view/one-vegasw
sites[.]google[.]com/view/onvg-ads-word
sites[.]google[.]com/view/oversmart/new
sites[.]google[.]com/view/pandareidel
sites[.]google[.]com/view/polajdasod6hbad
sites[.]google[.]com/view/ppo-ads
sites[.]google[.]com/view/quadrilhadohomemtanacasakaraio
sites[.]google[.]com/view/ricobemnovinhos
sites[.]google[.]com/view/s-ad-offica
sites[.]google[.]com/view/s-wppa
sites[.]google[.]com/view/sdawjj
sites[.]google[.]com/view/semcao
sites[.]google[.]com/view/sites-gb
sites[.]google[.]com/view/so-ad-reisd
sites[.]google[.]com/view/spiupiupp-go
sites[.]google[.]com/view/start-smarts
sites[.]google[.]com/view/start-smarts/homepage/
sites[.]google[.]com/view/umcincosetequebratudo
sites[.]google[.]com/view/vewsconnect
sites[.]google[.]com/view/vinteequatroporquarenta
sites[.]google[.]com/view/xvs-wods-ace
sites[.]google[.]com/view/zeroumnaoezerodois
sites[.]google[.]com/view/zeroumonlinecomosmp
Phishing domains
account-costumers[.]site
account-worda-ads[.]benephica[.]com
account-worda-ads[.]cacaobliss[.]pt
account[.]universitas-studio[.]es
accounts-ads[.]site
accounts[.]google[.]lt1l[.]com
accounts[.]goosggles[.]com
accounts[.]lichseagame[.]com
accousnt-ads[.]tmcampos[.]pt
accousnt[.]benephica[.]pt
accousnt[.]hyluxcase[.]me
ads-goo[.]click
ads-goog[.]link
ads-google[.]io-es[.]com
ads-overview[.]com
ads1.google.lt1l.com
ads1[.]google[.]veef8f[.]com
adsettings[.]site
adsg00gle-v3[.]vercel[.]app
adsgsetups[.]shop
advertsing-acess[.]site
advertsing-v3[.]site
as[.]vn-login[.]shop
benephica[.]pt
cacaobliss[.]pt
colegiopergaminho[.]pt
docs-pr[.]top
tmcampos[.]pt
vietnamworks[.]vn-login[.]shop



















