Modernizing Security Operations with Zero Trust Architecture on AWS
What is Zero Trust? Zero Trust is a strategic approach to cybersecurity that secures an organization by eliminating implicit trust and continuously validating every stage of a digital interaction. in another word is a security framework requiring all users, whether in or outside the organization's network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data. Zero Trust assumes that there is no traditional network edge; networks can be local, in the cloud, or a combination or hybrid with resources anywhere as well as workers in any location. Components user/application authentication device authentication Trust Pillars of Zero Trust User, Device, Network, Infrastructure, Application, Data, Visibility and Analytics, and Orchestration and Automation. •ZERO TRUST FOR WORKFORCE:- People such as employees , contractors, partners and vendors accessing work applications using their personal or corporate managed devices. This pillar ensures only the right users and secure devices can access applications •ZERO TRUST FOR WORKLOADS:-Applications running in the cloud, in datacenters and other virtualized environments that interact with one another. this pillar focuses on secure access when an api, a microservice or a container is accessing a database within an application ZERO TRUST FOR WORKPLACE: This pillar focuses on secure access for any and all equipment connecting to enterprise networks; such as user endpoints, physical and virtual servers, printers, cameras, hvac systems, kiosks, infusion pumps, industrial control systems and more Why in Cloud Increased Complexity Multi-cloud environments introduce additional layers of complexity, making traditional perimeter-based security models less effective Data Silos Data scattered across multiple clouds can create security blind spots if not managed holistically Evolving Threats The threat landscape is constantly evolving, requiring a dynamic and adaptive security approach AWS offered Services AWS Control Tower Establish and manage multi-account governance at scale Identity and Access Management (IAM) Centralize identity and access management across AWS resources AWS WAF & Shield Protect applications and services against DDoS attacks and web vulnerabilities Amazon GuardDuty & Inspector Provide centralized visibility and threat detection across AWS Automate security assessments for workloads AWS CloudTrail Provide detailed logs of AWS API calls and user activities Conclusion Zero Trust must have approach for every organizations to reduce business and data breach risk. We can achieve through Google cloud 's offered services to defined and implement strategy.
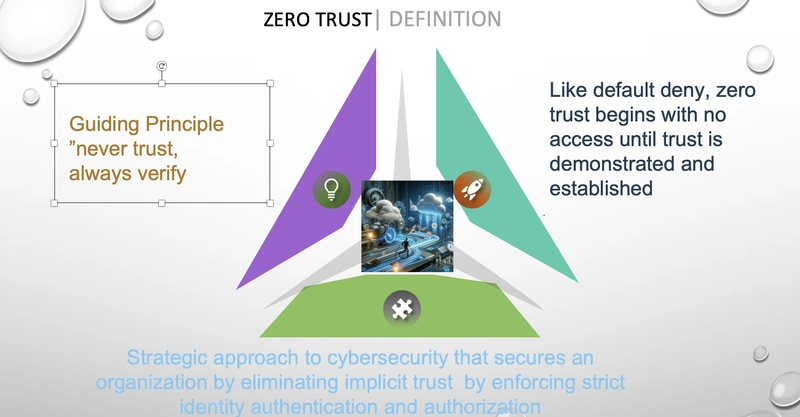
What is Zero Trust?
Zero Trust is a strategic approach to cybersecurity that secures an organization by eliminating implicit trust and continuously validating every stage of a digital interaction. in another word is a security framework requiring all users, whether in or outside the organization's network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data.
Zero Trust assumes that there is no traditional network edge; networks can be local, in the cloud, or a combination or hybrid with resources anywhere as well as workers in any location.
Components
user/application authentication
device authentication
Trust
Pillars of Zero Trust
User, Device, Network, Infrastructure, Application, Data, Visibility and Analytics, and Orchestration and Automation.
•ZERO TRUST FOR WORKFORCE:- People such as employees , contractors, partners and vendors accessing work applications using their personal or corporate managed devices. This pillar ensures only the right users and secure devices can access applications
•ZERO TRUST FOR WORKLOADS:-Applications running in the cloud, in datacenters and other virtualized environments that interact with one another. this pillar focuses on secure access when an api, a microservice or a container is accessing a database within an application
ZERO TRUST FOR WORKPLACE: This pillar focuses on secure access for any and all equipment connecting to enterprise networks; such as user endpoints, physical and virtual servers, printers, cameras, hvac systems, kiosks, infusion pumps, industrial control systems and more
Why in Cloud
Increased Complexity
Multi-cloud environments introduce additional layers of complexity, making traditional perimeter-based security models less effective
Data Silos
Data scattered across multiple clouds can create security blind spots if not managed holistically
Evolving Threats
The threat landscape is constantly evolving, requiring a dynamic and adaptive security approach
AWS offered Services
AWS Control Tower
Establish and manage multi-account governance at scale
Identity and Access Management (IAM)
Centralize identity and access management across AWS resources
AWS WAF & Shield
Protect applications and services against DDoS attacks and web vulnerabilities
Amazon GuardDuty & Inspector
Provide centralized visibility and threat detection across AWS
Automate security assessments for workloads
AWS CloudTrail
Provide detailed logs of AWS API calls and user activities
Conclusion
Zero Trust must have approach for every organizations to reduce business and data breach risk. We can achieve through Google cloud 's offered services to defined and implement strategy.