Debian LDAP Server Vulnerabilities Allow Attackers Authenticate as Users
The Debian Long Term Support (LTS) team has released a security update for the 389-ds-base LDAP server, addressing several critical vulnerabilities. Notably, An LDAP vulnerability CVE-2021-3652, affecting version 1.4.4.11-2 of the package, has now been resolved in the updated release for Debian 11 “Bullseye” (version 1.4.4.11-2+deb11u1). Users are strongly encouraged to update their systems promptly […] The post Debian LDAP Server Vulnerabilities Allow Attackers Authenticate as Users appeared first on Cyber Security News.

The Debian Long Term Support (LTS) team has released a security update for the 389-ds-base LDAP server, addressing several critical vulnerabilities.
Notably, An LDAP vulnerability CVE-2021-3652, affecting version 1.4.4.11-2 of the package, has now been resolved in the updated release for Debian 11 “Bullseye” (version 1.4.4.11-2+deb11u1). Users are strongly encouraged to update their systems promptly to mitigate potential security risks.
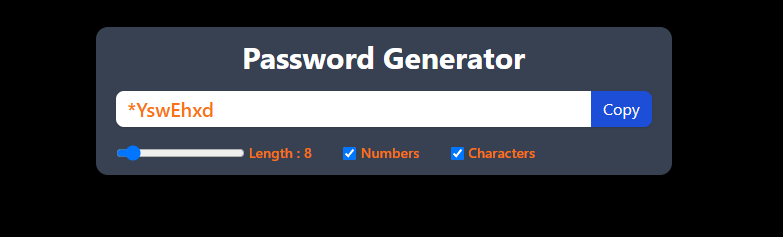
If an asterisk (*) is mistakenly or intentionally imported as a password hash, it can create a serious security issue. Instead of rendering the account inactive, any password entered during authentication will match successfully.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
This flaw allows attackers to authenticate as users whose passwords have been disabled, bypassing account security entirely.
The update addresses nine vulnerabilities, ranging from issues that allow unauthorized access to denial-of-service attacks. Below is a breakdown of each vulnerability.
CVE ID Description CVE-2021-3652 Mismanagement of password hashes containing an asterisk could allow any password to authenticate successfully, even if the account should be inactive. CVE-2021-4091 A double-free vulnerability in the handling of virtual attributes during persistent searches could lead to unexpected server crashes. CVE-2022-0918 A flaw in the handling of TCP connections allows unauthenticated attackers to crash the server with a single malicious message. CVE-2022-0996 Improper authentication due to expired passwords could allow unauthorized access to the database. CVE-2022-2850 A NULL pointer dereference in the content synchronization plugin enables authenticated attackers to trigger a denial of service. CVE-2024-2199 Malformed userPassword input could cause a server crash. CVE-2024-8445 Addresses an incomplete fix for CVE-2024-2199, ensuring all scenarios of malformed userPassword input are covered. CVE-2024-3657 A specially crafted LDAP query could cause server failure, leading to a denial of service. CVE-2024-5953 Malformed password hashes may result in a server denial of service when affected user accounts attempt to log in.
These vulnerabilities could allow attackers to gain unauthorized access to accounts, crash the directory server through crafted queries or malformed inputs, and cause a denial of service, thereby disrupting LDAP operations.
All users relying on the 389-ds-base LDAP server in Debian 11 “Bullseye” should update to version 1.4.4.11-2+deb11u1 immediately to protect their systems.
To apply the update, use the following commands:
sudo apt-get update
sudo apt-get install --only-upgrade 389-ds-baseBy staying up to date with security patches, organizations can safeguard their systems against the exploitation of these vulnerabilities.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
The post Debian LDAP Server Vulnerabilities Allow Attackers Authenticate as Users appeared first on Cyber Security News.
What's Your Reaction?